What is spoofing and how is it dangerous for my business?
Doctor Digital Says

Spoofing is a type of cyber attack that involves impersonating a legitimate entity in order to gain unauthorized access to data, systems, or networks. Spoofing attacks can take many different forms, but they all involve convincing a person to hand over sensitive information or click on a link that releases some kind of ransomware or malicious code to disrupt their business with the aim of getting money.
A common example is IP spoofing, where an attacker alters the source IP address in a network packet to make it appear as though the packet originated from a trusted source. A network packet is a unit of data that is transmitted over a computer network. It is like a digital envelope that contains information such as the source and destination addresses, the type of data being transmitted, and any other necessary information needed to transmit the data across the network. This can be used to bypass security controls, such as firewalls or access controls, and gain access to sensitive data or systems. This tends to be used with large organisations where there is a weakness or a human error that allows the bypass to happen.
Another example is email spoofing, where an attacker sends an email that appears to come from a trusted source, such as a bank or a colleague. This can be used to trick the recipient into providing sensitive information, such as login credentials or financial information or to click on a link that looks legit but is corrupted.
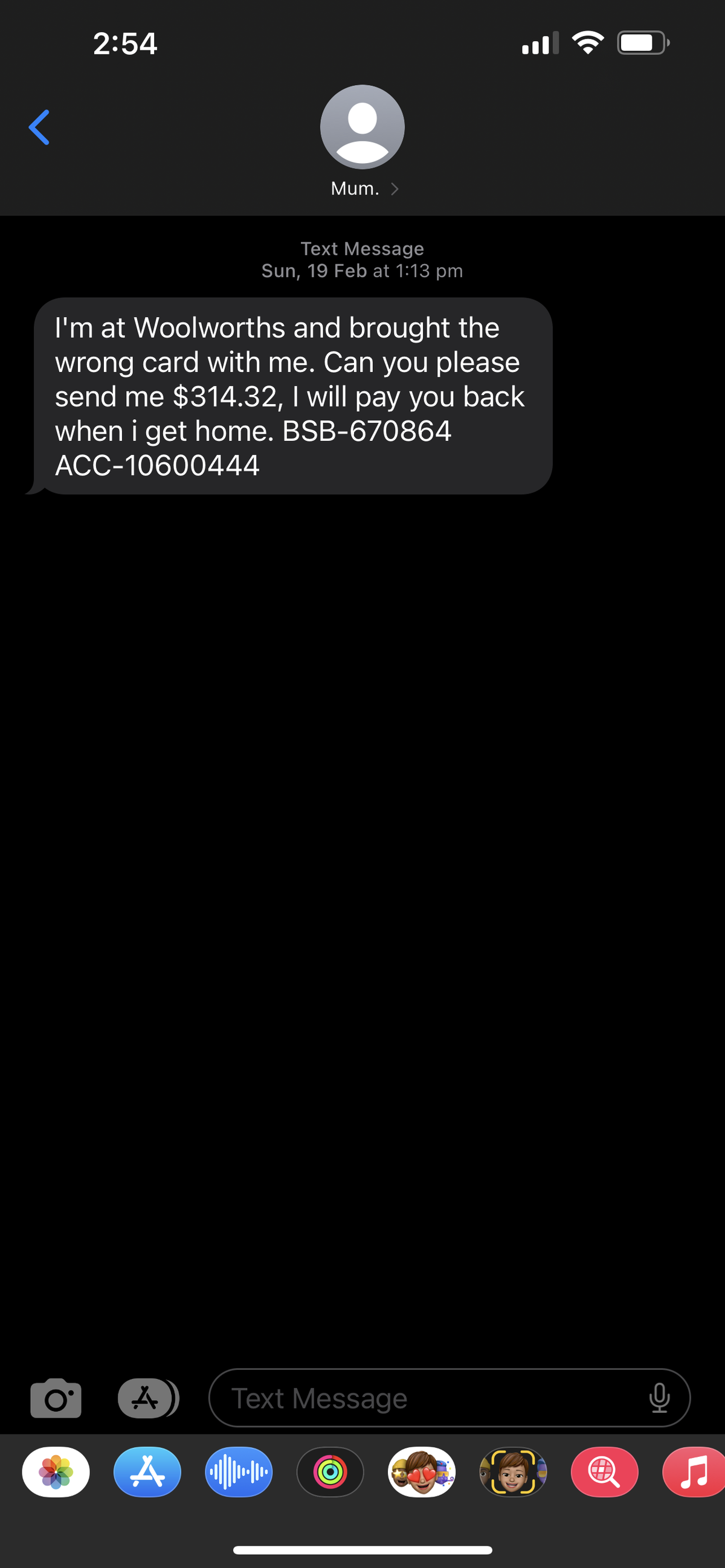
One of the more successful methods of spoofing is to use text messages. This type of attack is becoming more and more common. In SMS spoofing, an attacker sends a text message that appears to come from a trusted source, such as a bank or a service provider, or a parent, child or sibling.
The cyber attacker might send a text message that appears to be a credible message from a bank, even appearing in a previous text chain from the bank, asking the recipient to provide personal or financial information or call a call centre which seems to be a legitimate entity. The attacker then uses information revealed by the victim for identity theft or to gain access to the victim's bank account. SMS spoofing is also often hidden in fake messages from social media platforms (your account has been disabled) or delivery services (your parcel needs collection) which seem urgent, and personalised, and are often barely detectable from the real thing.
All forms of SMS spoofing can be difficult to detect. The critical factor in the success of all spoofing activities is the attacker relying on the victim to not be paying attention. Small business is very susceptible to these type of attacks as small business owners and staff are often busy, multitasking, and trusting of known and major brands such as Instagram or a big four bank. As most of these messages require urgent action, and often involve business-critical platforms or accounts, the first action is often to fix the problem, rather than take a moment to fact check, verify the communication using a different channel, or observe any anomalies in the request.
There are tried and true ways to protect against spoofing as mentioned, such as verifying the sender's identity before providing any sensitive information or clicking on links. Additionally, users can enable two-factor authentication, which requires a code sent via text message in addition to a password, to add an extra layer of security. It is rare any credible organisation will ask for identifying material outside of a secure web page, but if it feels odd, its likely to be, so be alert, and mildly alarmed.
Unfortunately the news isn't getting better. With mass cyberattacks in Australia in 2022 releasing millions of pieces of personal data, even very amateurish cyber criminals have access to enough information to spoof you and put ransomware on your business accounts. With an estimated $4 billion dollars to be lost in Australia 2023 to cyber criminals, cyber-attacks are serious and everyone needs to be alert to what channels they trust and how they do business. Think about the impacts on your business if your social pages were hijacked, or your accounts were emptied of cash.
These types of events are devastating and very little can be done to support businesses as often they have given the attackers access, voiding the responsibility of banks etc to be able to intervene until it is too late. There has never been a better time to audit your cyber security processes and get your security tight across all of your devices and platforms.
Need to get back to basics? Our Digital Ready Fundamentals course is designed to give you all you need to get on track in a quick, easy, actionable video format - including a cybersecurity primer. Join Doctor Digital and get fundamental to get the best out of your Digital Ready coaching experiences.


