Introduction

In this factsheet we look at the critical benefits of MFA as part of your first line of defence against cyber-attacks, and cover how to turn it on for all of the common platforms, social media, shopping, services and gaming.
Multi-factor authentication (MFA) has become a critical component of business security in the digital age. With cyber threats growing in complexity and sophistication, relying solely on often weak and easily cracked passwords for authentication is no longer sufficient. The primary reason why MFA is crucial to business security is its effectiveness in preventing unauthorised access to sensitive data and systems. Even if an attacker manages to obtain or guess a user's password, MFA acts as a robust defence mechanism. By requiring a second form of authentication, such as a unique code generated on a mobile device, MFA significantly reduces the risk of unauthorised access. It ensures that even if the password is compromised, the attacker would still need the additional factor to gain entry, adding an extra layer of protection against data breaches, unauthorised account access, and identity theft.
Additionally, MFA offers businesses enhanced protection against phishing attacks. Phishing is a common method used by cybercriminals to trick individuals into divulging their credentials or sensitive information. With MFA in place, even if an employee falls victim to a phishing attempt and unknowingly provides their password, the attacker would still be unable to access the account without the additional authentication factor. MFA acts as a reliable safeguard against such attacks, mitigating the risk of unauthorised access and reducing the chances of data loss or financial damage.
Video presentation: All about Multi Factor Authentication (MFA)
What is MFA?
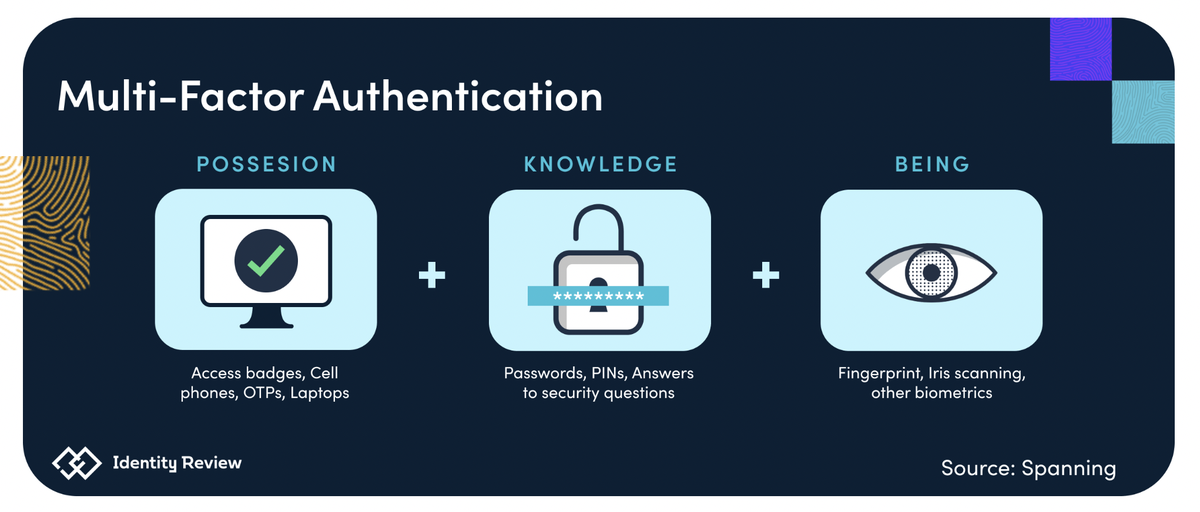
At its most basic, MFA is when you use two or more different types of actions to verify your identify, you may already be using MFA as many services now require it as standard - for example, when you receive an authentication code by SMS text message after entering your password to log into an online account like banking or Xero. MFA often goes by different names. You may see it called two-factor authentication (2FA) or two-step verification.
Think of adding MFA to your account like adding a house alarm that requires a PIN to deactivate. It provides you with an extra layer of protection from cybercriminals trying to break in. Even if they break through one layer (for example, by guessing your password), they still need to break a second barrier to access your account.
Having an extra step can be inconvenient at first but remember that taking shortcuts leaves your system more vulnerable. You are better off spending a few seconds entering a one-time code now, to avoid spending hours later on trying to regain access to your accounts and dealing with the consequences of your data being stolen.
MFA isn't the only authentication method you may have heard about. Two-Factor Authentication (2FA) is a subcategory of MFA. It is widely used for digital banking, social media and e-commerce. Consumers commonly encounter 2FA when withdrawing money from an ATM—here, a user inputs a debit card (a factor the user possesses), along with a PIN (a factor the user knows) to successfully gain access. 2FA follows the same factors as MFA (knowledge, possession, inherence), but chooses two instead of multiple.
Single Sign On (SSO) is another common authentication technique that allows users to gain access across multiple applications or websites with a single set of credentials. The SSO framework is based on a trust certificate between the service provider and the identity provider. This certificate is typically composed of identifying pieces of information about a user, such as a username or an email, ensuring the information being sent to the service provider is from a secure source. The steps of SSO are typically as follows:
- A user navigates to the website they want to gain access to (service provider)
- The service provider sends the certificate that holds a user’s email address or username to the identity provider to authenticate themselves
- The service provider will check if the user has already been authenticated. If the user has previously logged in, then the service provider will send back a token authentication to the user
- If the user has not logged in before, they will be prompted to provide further information such as an one time password (OTP)
- Once the credentials are deemed valid and have been processed, the user will receive a token, allowing them to access the service.

Turning on MFA for your critical accounts
You should turn on MFA wherever possible, starting with your important accounts, such as:
- User and email accounts, since a cybercriminal with access to your email accounts can reset passwords for your other accounts.
- Financial services, such as your online banking.
- Accounts that save or use your payment details (e.g. eBay, Amazon, PayPal).
- Social media accounts (e.g. Facebook, Instagram).
- Any other accounts that hold personal information (e.g. myGov).
How to turn on MFA depends on the software or service you are using, however the steps are somewhat similar for most applications. The following list of websites and apps by the Australian Cyber Security Centre are examples of important accounts that you should protect with MFA. Each link provides instructions on how to set up MFA for that service.
User and email accounts
Financial services
Online shopping
Social media and communication
Facebook and Facebook Messenger
Government services
Gaming
Conclusion
Multi-factor authentication (MFA) has quickly become a superhero for cybersecurity. MFA allows you to protect your business by requiring at least one additional security identifier on top of your username and password in order to get access to an online account or application. Though deceptively simple, multi-factor authentication is also shockingly effective, and working your way through the links about to set your business accounts up to be protected will pay off the investment of time infinitely when you know you have made it that much harder for cybercriminals to get access to your most precious digital assets.

