Introduction

It seems that the news of cybercrime against all sizes of businesses is becoming a daily news report, with losses to individuals and businesses in Australia predicted to pass a trillion dollars. Former Cisco CEO John Chambers in a 2015 World Economic Forum speech summed up the predicament of businesses presciently when he said all those years ago that "there are two types of businesses, those who have been hacked, and those who don’t yet know they have been hacked." Taking the threat of cybercrime seriously is critical for businesses to prepare and risk manage the inevitability of a hack or attack attempt or success. While it might sound threatening and overwhelming, the reality is it is the digital equivalent to putting an alarm on your business, securing the windows and doors, and knowing how to keep your cash and stock safe. Being clued up on the changing cyber threat landscape and keeping yourself and your staff trained to use simple strategic fixes to proactively insulate your business from threats is the best approach, and ultimately a little investment in time to learn, and deploy upfront saves headaches and heartache if you are a victim of a successful attack.
Video presentation: Malware! What you need to know
What is Malware?
The John Chambers quote exemplifies a stark reality: Cybercrime is easier than ever to perpetrate, thanks to the internet and the proliferation of digital devices, also known as endpoints. Criminals can find kits containing pre-built malware for as little as a few dollars online and get started on a lucrative career destroying your business. These criminals can and are located everywhere, and despite the Australian + Tasmanian government and its agencies taking cyber security very seriously, it is a difficult beast to control with hundreds of thousands of hackers globally using sophisticated methods to stay anonymous and hard to convict.
One of the primary ways that hackers get access to your data and creep into your devices is Malware. Malware, short for malicious software, refers to any software or code that is specifically designed to harm, exploit, or gain unauthorised access to computer systems, networks, or devices. Malware is created by cybercriminals with malicious intent, and its primary goal is to compromise the security, integrity, or availability of digital assets, steal sensitive information, or disrupt normal operations.
Organisations with inadequate IT security are particularly vulnerable, and these tend to be small businesses. Cyberattacks have also grown in sophistication and complexity. The days of simply relying on your computer’s built-in antivirus software are over. Businesses need the best endpoint security software to remain protected.
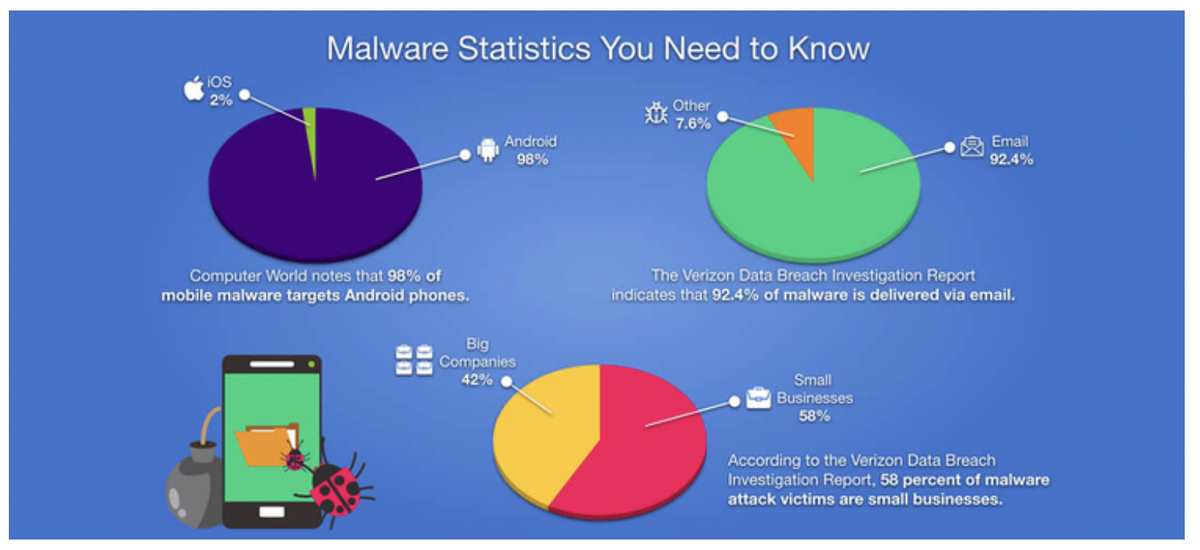
Meet the Malware
To understand the damage malware can inflict, let's take a look at the top 10 malware attack types.
- Viruses: Viruses are programs that replicate themselves by infecting other files or systems. They can spread rapidly and often require user interaction, such as opening an infected file or executing a malicious program.
- Worms: Worms are self-replicating programs that spread without user intervention. They exploit vulnerabilities in networks or systems to propagate and can cause widespread damage by consuming network bandwidth or carrying out malicious actions.
- Trojans: Trojans are deceptive programs disguised as legitimate software or files. Once installed or executed, they can provide unauthorised access to an attacker, steal sensitive data, or enable other malware to be installed.
- Polymorphic Malware: Polymorphic malware is designed to constantly change its code structure, making it difficult for traditional antivirus programs to detect and eradicate. It can adapt its characteristics to avoid detection and hinder analysis.
- Ransomware: Ransomware encrypts files on a victim's system and demands a ransom in exchange for the decryption key. It can quickly encrypt a large number of files, rendering them inaccessible until the ransom is paid.
- Rootkits: Rootkits are designed to gain privileged access and control over a system. They hide their presence and provide unauthorised access to an attacker while remaining undetected by traditional security measures.
- Keyloggers: Keyloggers record keystrokes made by a user, capturing sensitive information such as login credentials, credit card numbers, or personal messages. This information is then sent to an attacker, who can misuse it for fraudulent activities.
- Bots: Bots are software programs that run automated tasks over the internet. When controlled by an attacker, they form a botnet, which can be used for various malicious activities, including distributed denial-of-service (DDoS) attacks or spam email distribution.
- Spyware and Adware: Spyware silently gathers information about a user's activities, such as browsing habits, login credentials, or personal data. Adware, on the other hand, displays unwanted advertisements, often in the form of pop-ups or banners, on a user's device. Both spyware and adware can compromise user privacy and security.
- Mobile Malware: With the proliferation of mobile devices, malware targeting smartphones and tablets has become prevalent. Mobile malware can compromise device security, steal personal information, or send unauthorised premium SMS messages, among other malicious activities.
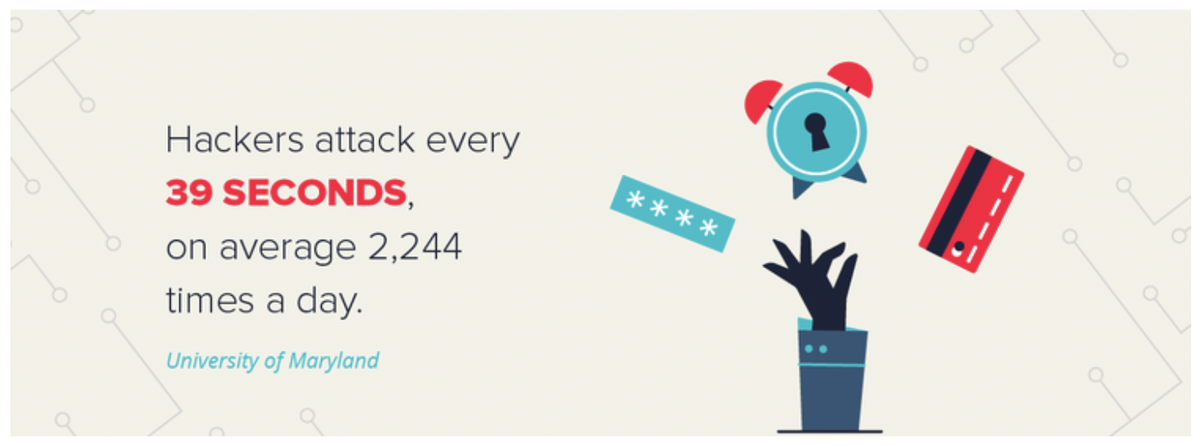
Conclusion
These are just a few examples of the many types of malware that exist today. Malware can be distributed through various means, such as email attachments, malicious websites, compromised software, infected removable media, or exploiting vulnerabilities in software or operating systems. To protect against malware, it is essential to have robust security measures in place, including antivirus software, firewalls, regular software updates, user education on safe computing practices, and proactive monitoring for suspicious activities.
Cybercriminals continuously evolve their attacks to evade detection and improve their ability to infect devices. For instance, malware traditionally infected computer files but is increasingly moving to a fileless malware approach that leaves no obvious trace. This makes it difficult to detect and remove even if your organization has a security operations center.
To keep pace, adopt endpoint security software. Endpoint protection is a must for any business. These software platforms not only include antivirus and other protection layers designed to stop the malware threats on this list, but they also highlight IT network vulnerabilities to proactively strengthen your security. Complement this with endpoint detection and response capabilities to catch threats that slip through your defenses. EDR, alongside endpoint protection software, delivers a holistic security solution and keeps the various types of malware at bay.

